With rapidly growing technology, it has become exponentially easy for the workforce to do their task more efficiently. One of the key contributors to this is access to organizational resources anywhere through various Mobile Devices.
As per a study by Hotdesign, company employees and executives are more inclined on using multiple devices for more work flexibility which primarily includes smartphones.
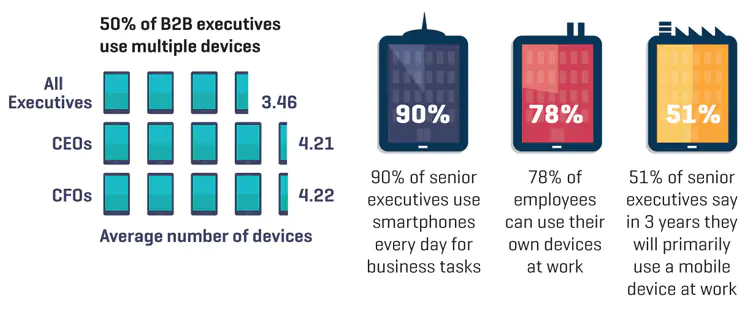
A survey by Hotdesign.com showing the use of mobile devices for work.
But with the convenience, these mobile devices bring their own challenges and create loopholes which makes the organizational resources vulnerable in terms of security. As per the study by Heimdal Security and Statista, cyber security crimes accounted for millions of dollars of loss globally. Cyber attacks are very hard to detect and majority of the losses are unrecoverable. The same study also suggests that 170 days is the average time required to detect the attack and 68% of the losses are not recoverable.
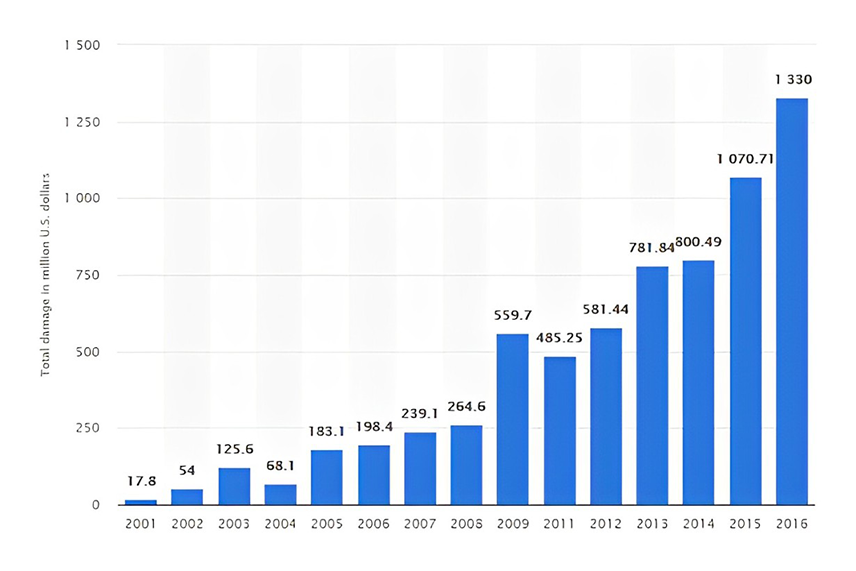
Amount of monetary damage caused by reported cyber crime to the IC3 from 2001 to 2016 (in million U.S. dollars) from a study by Stastista
“Imagine the power of the HR system: It has full names, dates of birth, Social Security numbers, pay rates, employee bonuses and annual reviews,” says Chris Hadnagy, CEO of Social-Engineer Inc. and author of Social Engineering: The Art of Human Hacking (Wiley, 2010).
“It holds all the keys to the kingdom for the company.” Imagine this key being accessed using few buttons on your mobile devices. Thus, before the HR systems are made accessible through Mobile Devices the organization should be well prepared and plan mobile device policies and access management. This makes Mobile Device Management and Identity Access Management the primary mechanisms for HR mobile app security. In the next blog series we will talk on these two mechanisms in detail.